Introduction
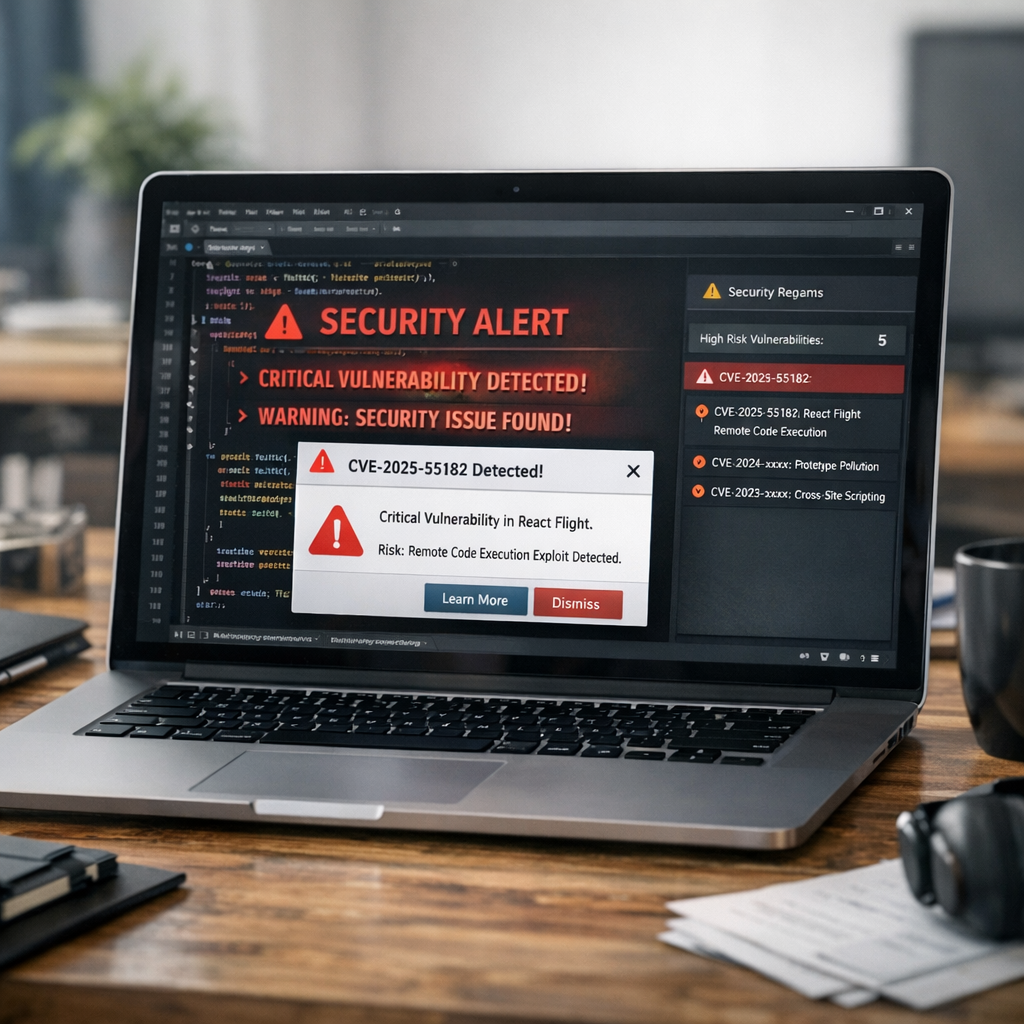
A critical vulnerability affects the React Flight protocol, at the heart of Server Components. Its potential impact is major: a simple request can expose a server to unauthorized code execution. Here is what to understand and how to respond.
Context and scope of the vulnerability
The CVE-2025-55182 flaw is described as critical, with a direct exploitation scenario via the Server Components transfer protocol. The main risk: turning a harmless HTTP request into server-side code execution, without authentication.
Warning
An endpoint exposing React Flight can become an entry point for code execution if vulnerable versions are used.
React Flight in brief
React Flight serializes server-side components to send them to the client. The problem arises when malicious payloads are deserialized without strict validation, opening the door to unexpected object creation and dangerous calls.
Key point
The risk comes from deserializing untrusted data in a server context.
// Example of environment check before exposing an endpoint
if (process.env.NODE_ENV === "production") {
enableServerComponentsEndpoint();
}How exploitation is possible
An attacker can craft a React Flight payload to force the server to rebuild an abnormal object graph. This can lead to indirect calls to sensitive APIs, then to arbitrary code execution.
// Strict validation of a payload before processing
function isValidFlightPayload(payload) {
return typeof payload === "string" && payload.length < 200000;
}Warning
Direct exposure of a Flight endpoint without additional controls greatly increases the attack surface.
Real-world impacts for teams
The impact translates into possible compromise of application servers, resource hijacking (mining, backdoor), and a risk of data leakage. The number of affected applications is high, especially via popular frameworks.
Alert signal
Exploitation attempts can appear quickly after public disclosure.
// Example of logging access to a sensitive endpoint
app.post("/_flight", (req, res) => {
auditLogger.info("Flight endpoint accessed", { ip: req.ip });
handleFlight(req, res);
});Recommended mitigation measures
The priority is to update the affected dependencies and reduce endpoint exposure. A quick version audit and network monitoring are essential.
Good practice
Enable payload size controls and server-side guardrails.
// Example of request size limiting
app.use(express.json({ limit: "200kb" }));Conclusion
The CVE-2025-55182 flaw is a reminder that server-side deserialization remains a critical vector. Updating, reducing exposure, and adding defensive controls are the best levers to limit risk.